Sunbird has been promising iMessage support on Android for about a year now, but the company has always seemed rather sketchy. Now, as Nothing Chats, built on Sunbird, has launched, the privacy nightmare is coming true – not only is the app not end-to-end encrypted as promised, but image files from other users are pretty easy to access in plain text.
The promise of Sunbird and, in turn, Nothing Chats is to deliver iMessage support to Android. This is done by having users log into their Apple ID through the app which routes the login through a Mac server farm. It’s not a unique method, but the big differentiator here is that Sunbird has made a big deal out of claiming that end-to-end encryption is kept in place throughout the whole process.
On Sunbird’s website it directly says:
The Sunbird servers do not store user data promoting a safe, secure, and private messaging environment. With end-to-end encrypted, confidential messaging, Sunbird is fully secure and completely private.
By adding encryption between Android and iMessage where there currently is none, Sunbird is the first of its kind to give a unified and safe messaging experience to Android users.
Nothing reiterates this on a landing page for Nothing Chats, saying:
…Nothing Chats is built on Sunbird’s platform and all Chats messages are end-to-end encrypted, meaning neither we nor Sunbird can access the messages you’re sending and receiving.
But, that’s just not true.
Frightening new findings reveal that Sunbird and Nothing Chats are, in fact, not fully end-to-end encrypted, as user data can be accessed in plain text.
“Wukko” on Twitter/X published findings that Nothing Chats sends all media attachments, including user images, to Sentry with links to those attachments visible in plain text. Further, “all” data is sent and stored through Firebase, and it’s also completely unencrypted.
9to5Google can independently confirm Wukko’s findings.
In our Dylan Roussel’s research, we found that once a user authenticates with the JSON Web Tokens (JWT) that are insecure in transit, they can access Nothing Chat’s Firebase database and see messages and files from other users sent in real-time and in plain text. He particularly calls out that vCards are accessible, as these directly include user names, phone numbers, email addresses, and sometimes even more personal data.
He mentions that over 630,000 media files are currently stored by Sunbird via Firebase including images, videos, PDFs, audio, and more. So, while it’s true that Sunbird doesn’t store user data on its own servers, data is very much being stored.
Dylan further explains his findings in a thread on Twitter/X.
The folks over at Texts.com have also broken this process down in detail.
In a blog post, it’s pointed out that it takes a very short bit of code to automate the process of downloading this information. A demo of an iMessage being sent, only for the database to show that “end-to-end encrypted” text in plain text was also shown, as seen below. A proof of concept was also created and published to Github to show how it all works.
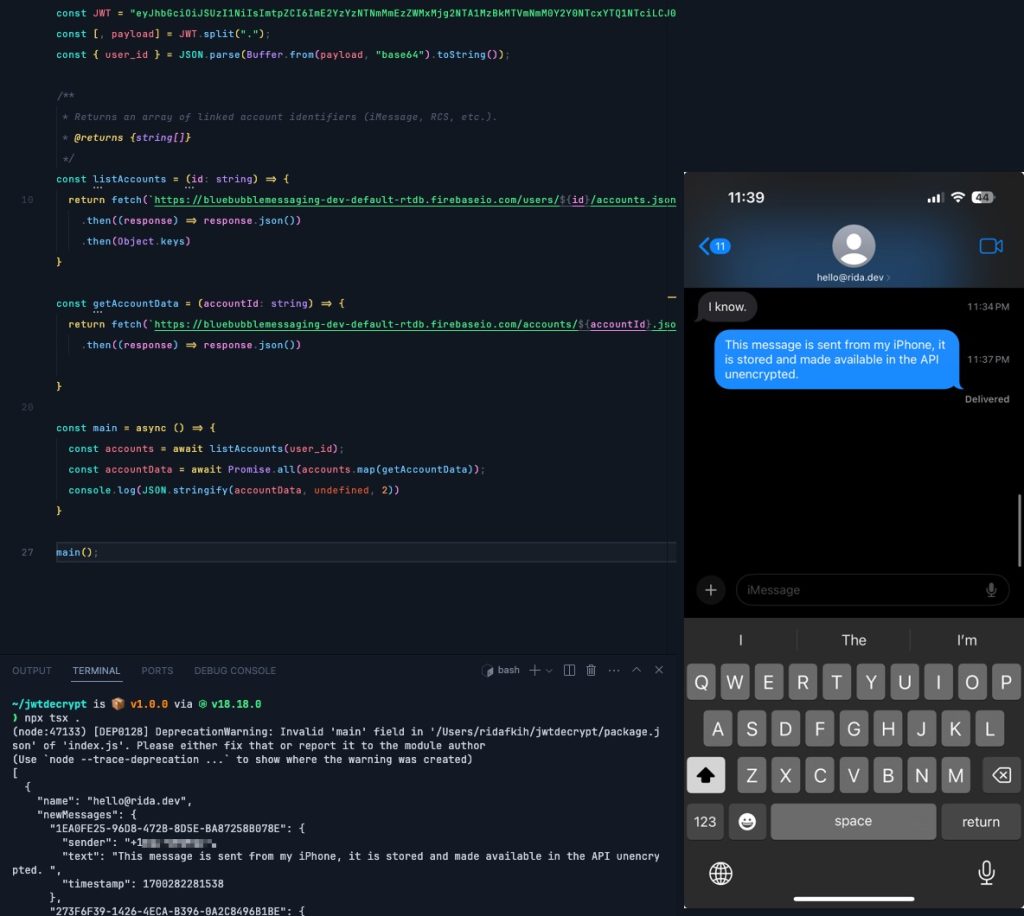
Yikes.
We first discovered this, for lack of a better term, privacy nightmare late on November 17 and immediately notified Nothing (via public relations, as the company has no point of contact for security problems) due to the very sensitive nature of this vulnerability – user data is literally on the line here and completely insecure.
Update: Nothing has confirmed to 9to5Google that it has pulled Nothing Chats from the Play Store and will be “delaying” the launch to “fix several bugs.” A Nothing spokesperson says:
We’ve removed the Nothing Chats beta from the Play store and will be delaying the launch until further notice to work with Sunbird to fix several bugs. We apologize for the delay and will do right by our users.
What remains unclear at this point is how this will affect Sunbird’s app, as it has these same issues as evidenced by the hundreds of thousands of media files already in the Firebase database.
However, in the time since we reached out, it seems Nothing and Sunbird may have blocked downloads of the app in the Play Store. Nothing Chats is not showing up in Play Store search, and when navigating to the listing directly on multiple Nothing Phone (2) units, the app was listed as “not available in your country” as pictured above and unable for download, which appears to have changed in the past several hours as the app was available for users yesterday after around Noon ET.
9to5Google’s Take
As far as privacy issues go, this is about as bad as it gets.
Top comment by Gordon Lutz
From what I've read on forums it didn't sound like anyone even got the app to actually work period.
I couldn't even create an Apple ID no matter what I tried, kept getting a message saying it couldn't be done at this time.
The app didn't look that great anyways.
Not only are image files accessible, but everything is out there and shockingly easy to find. It’s unimaginably terrifying for your private data really, and goes way beyond the concern everyone had of someone just having access to your Apple ID.
While this ultimately is on Sunbird as it built out the infrastructure and the Nothing Chats app, Nothing’s lack of due diligence here is worrying. If a vulnerability like this could be found in less than 24 hours from multiple users, how did Nothing miss it in the months this partnership was likely being built out? And, beyond that, will something even worse be discovered over time?
It goes without saying at this point, but you absolutely should not download Nothing Chats or Sunbird.
Dylan Roussel contributed to this article.
FTC: We use income earning auto affiliate links. More.




Comments