
Besides the Samsung Exynos modem issue, Android 13 QPR2 with the March 2023 security update fixes a vulnerability with the Pixel’s Markup screenshot tool.
Dubbed “aCropalypse,” Simon Aarons identified and reported this vulnerability (CVE-2023-21036) to Google in early January, with the initial proof-of-concept exploit developed by David Buchanan:
Screenshots cropped using the built-in “Markup” app on Google Pixel devices may be retroactively un-cropped and un-redacted under many circumstances.
aCropalypse FAQ (coming soon)
The built-in Markup utility, released with Android 9 Pie in 2018, found on Pixel phones lets you edit (crop, add text, draw, and highlight) screenshots.
The problem
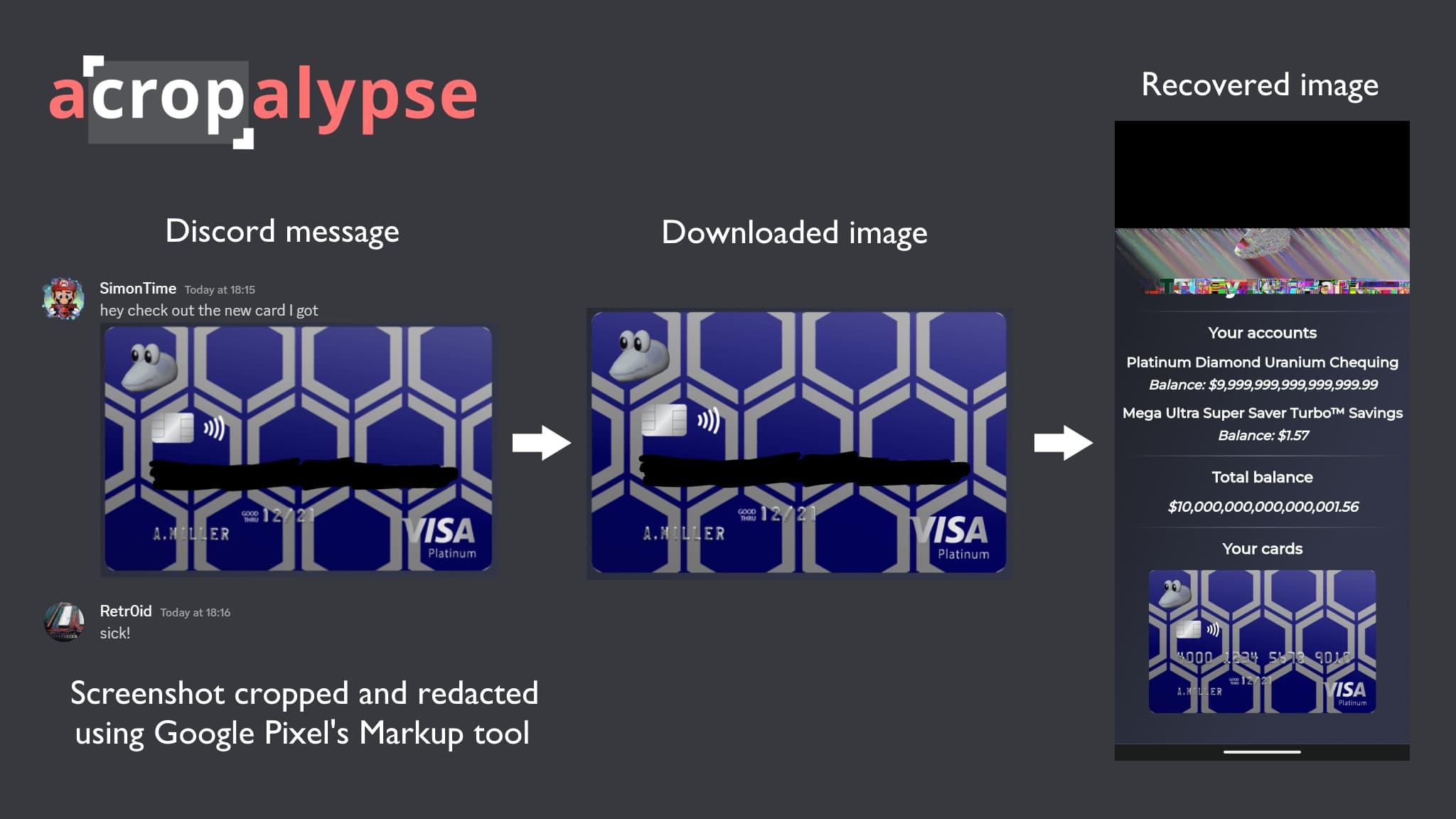
For example (as shared on Twitter), let’s say you upload a screenshot from a hypothetical bank app/website that includes a picture of your credit/debit card. You crop out everything save for the card and then use Markup’s Pen tool to black out the 16-digit number. You then share that message on a service, like Discord.
Given a vulnerability in how Markup works, somebody that downloads the image is able to perform a “partial recovery of the original, unedited image data of [the] cropped and/or redacted screenshot.” In the above case, a malicious party can remove the black lines and see the credit card number, as well as ~80% of the full screenshot, which might include other sensitive information.
”The top 20% of the image is corrupted, but the remainder of the image – including a photo of the credit card with its number visible – is fully recovered.”
This might be an issue if you shared screenshots with addresses, phone numbers, and other private info.
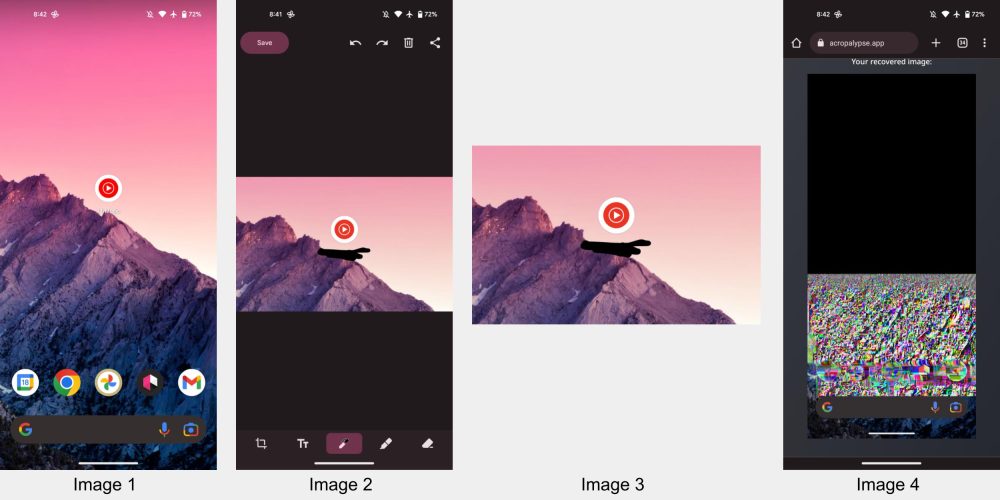
1: Original screenshot | 2: In Markup | 3: Cropped and drawn on image | 4: Using demo tool
What screenshots are affected?
The privacy impact of this bug stems from people sharing cropped images [that] unknowingly included extra data. Fortunately, most social media services re-process uploaded images, which strips the trailing data and mitigates the vulnerability. For example, Twitter is safe from acropalypse. The following is an incomplete list of known vulnerable services and apps commonly used to share images: (i.e. services that do not strip trailing image data)
aCropalypse FAQ (coming soon)
- Discord (as of the 17th of January, newly uploaded images are stripped of trailing data – however, any screenshot sent prior to that date is still vulnerable) (It’s unknown whether Google coordinated with Discord to make this change, or if it was coincidental)
At the moment, screenshots uploaded to Discord before mid-January 2023 — a change to the service was made then — are known to be affected.
There is a demo tool where you can upload a screenshot and see if a previously shared image is impacted.
Technical explanation
When an image is cropped using Markup, it saves the edited version in the same file location as the original. However, it does not erase the original file before writing the new one. If the new file is smaller, the trailing portion of the original file is left behind, after the new file is supposed to have ended.
aCropalypse FAQ (coming soon)
The technical write-up with root cause analysis is available, and a FAQ is forthcoming.
The issue in Markup was fixed with the March 2023 security patch, with CVE-2023-21036 listed as having a “High” severity. That Pixel update is currently available for the Pixel 4a-5a, 7, and 7 Pro.
Updating…
Thanks David
FTC: We use income earning auto affiliate links. More.




Comments