
Last year, Google announced Android Open Source Project (AOSP) support for Rust, and today the company provided an update, while highlighting the decline in memory safety vulnerabilities.
Google says the “number of memory safety vulnerabilities have dropped considerably over the past few years/releases.” Specifically, the number of annual memory safety vulnerabilities fell from 223 to 85 between 2019 and 2022. They are now 35% of Android’s total vulnerabilities versus 76% four years ago. In fact, “2022 is the first year where memory safety vulnerabilities do not represent a majority of Android’s vulnerabilities.”
That count is for “vulnerabilities reported in the Android security bulletin, which includes critical/high severity vulnerabilities reported through our vulnerability rewards program (VRP) and vulnerabilities reported internally.”
During that period, the “amount of new memory-unsafe code entering Android has decreased.”
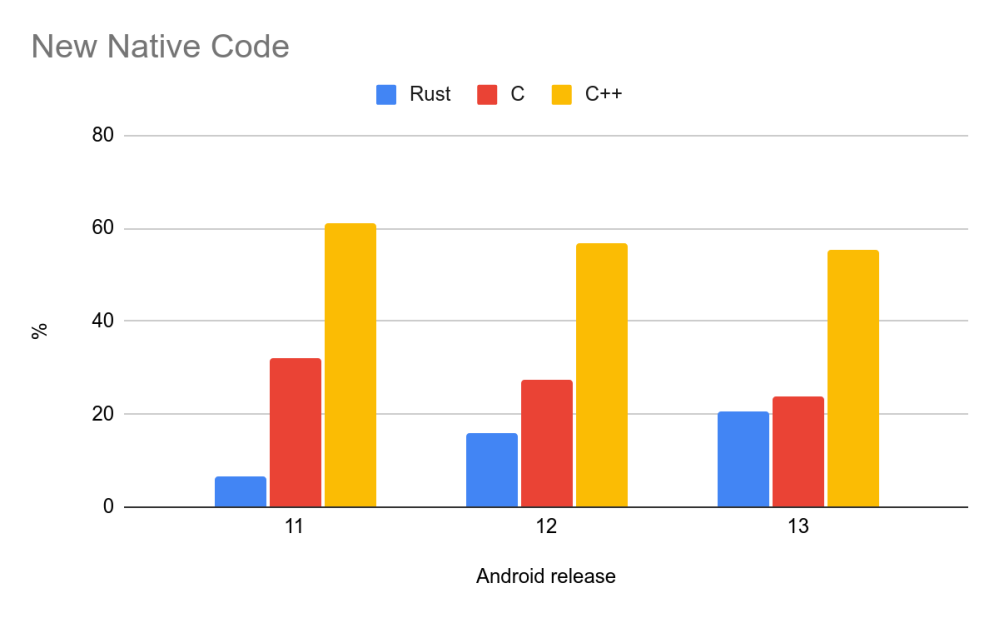
Android 13 is the first Android release where a majority of new code added to the release is in a memory safe language.
Rust makes up 21% of all new native code in Android 13, including the Ultra-wideband (UWB) stack, DNS-over-HTTP3, Keystore2, Android’s Virtualization framework (AVF), and “various other components and their open source dependencies.” Google considers it significant that there have been “zero memory safety vulnerabilities discovered in Android’s Rust code” so far across Android 12 and 13.
While correlation doesn’t necessarily mean causation, it’s interesting to note that the percent of vulnerabilities caused by memory safety issues seems to correlate rather closely with the development language that’s used for new code. This matches the expectations published in our blog post 2 years ago about the age of memory safety vulnerabilities and why our focus should be on new code, not rewriting existing components.
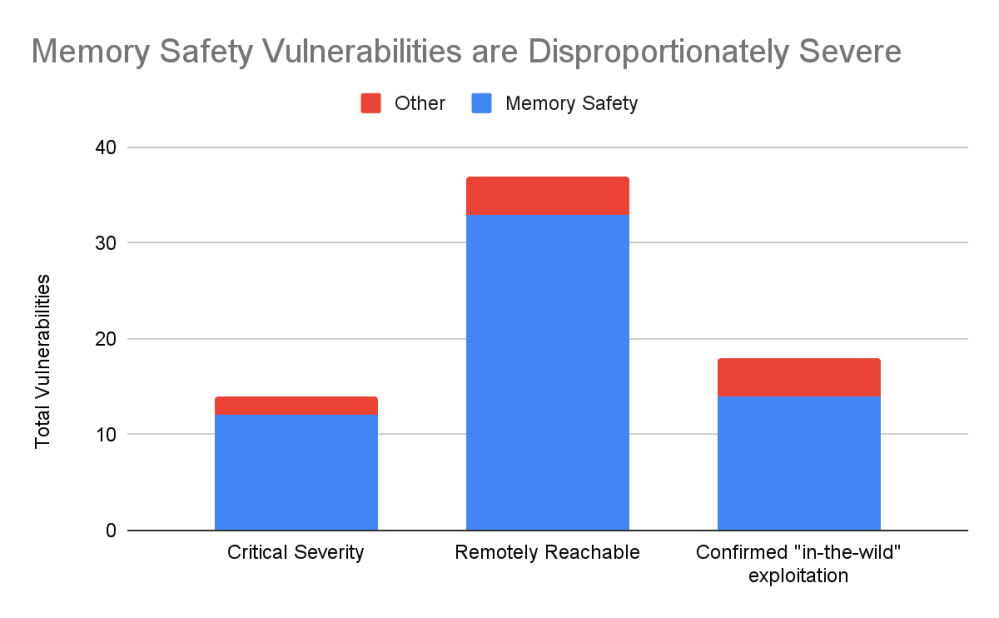
Google’s blog post today also talks about non-memory-safety vulnerabilities, which are less severe, and its future plans:
Migrating away from C/C++ is challenging, but we’re making progress. Rust use is growing in the Android platform, but that’s not the end of the story. To meet the goals of improving security, stability, and quality Android-wide, we need to be able to use Rust anywhere in the codebase that native code is required. We’re implementing userspace HALs in Rust. We’re adding support for Rust in Trusted Applications. We’ve migrated VM firmware in the Android Virtualization Framework to Rust. With support for Rust landing in Linux 6.1 we’re excited to bring memory-safety to the kernel, starting with kernel drivers.
FTC: We use income earning auto affiliate links. More.







Comments