Ahead of Android 14’s stable launch, Google is detailing “first-of-its-kind” cellular connectivity security features in the release.
At a high level, Google says the “Android Security Model assumes that all networks are hostile to keep users safe from network packet injection, tampering, or eavesdropping on user traffic.”
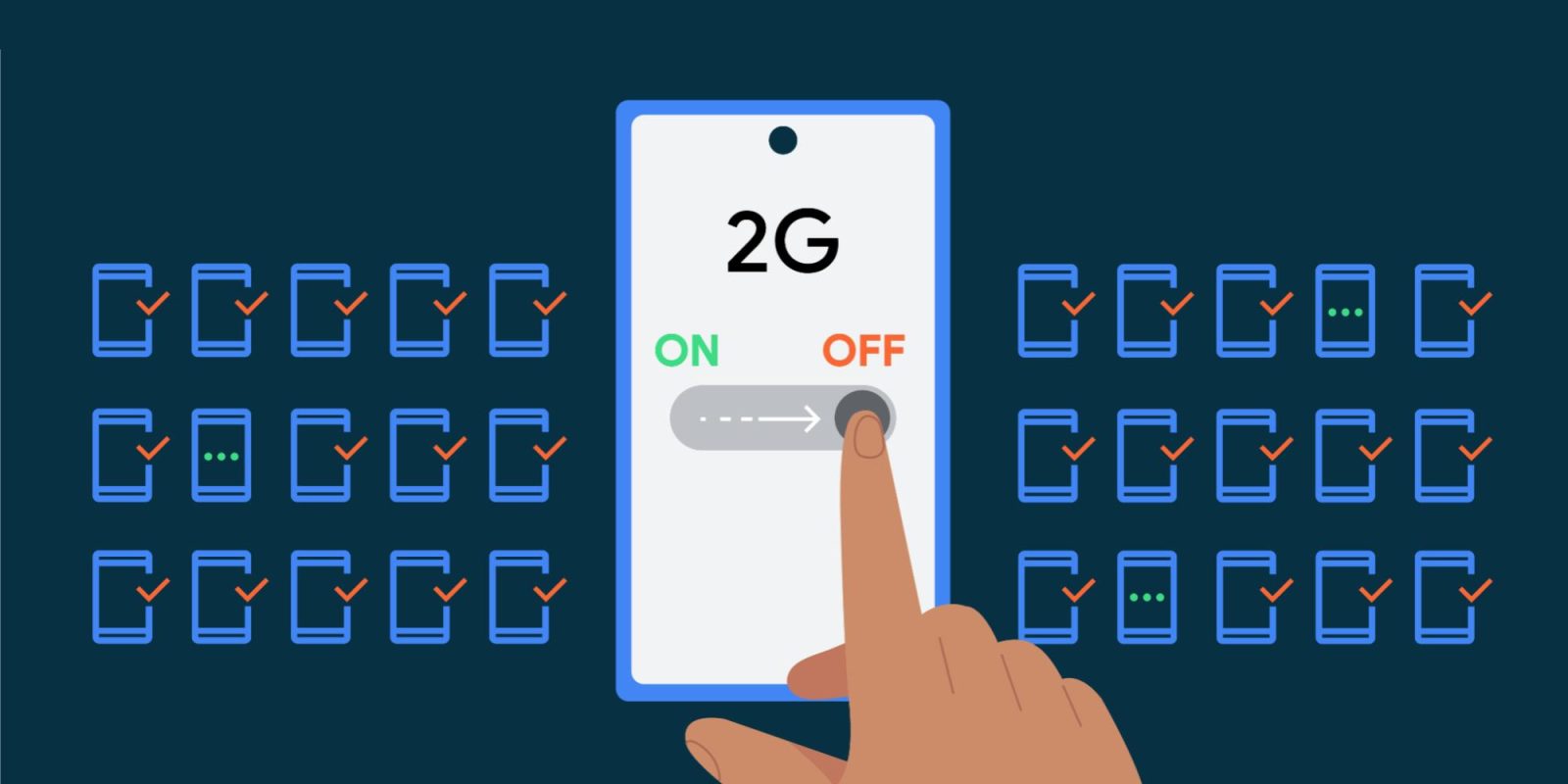
With Android 12, Google introduced an “Allow 2G” toggle — on Pixel: Settings > Network & internet > SIM(s) — that lets end users disable 2G at the modem level. The Pixel 6 was the first to adopt this, and “it is now supported by all Android devices that conform to Radio HAL 1.6+.”
In the United States, for example, most major carriers have shut down 2G networks. However, all existing mobile devices still have support for 2G. As a result, when available, any mobile device will connect to a 2G network. This occurs automatically when 2G is the only network available, but this can also be remotely triggered in a malicious attack, silently inducing devices to downgrade to 2G-only connectivity and thus, ignoring any non-2G network. This behavior happens regardless of whether local operators have already sunset their 2G infrastructure.
On Android 14, admins of Android Enterprise-managed business and government devices can “restrict a device’s ability to downgrade to 2G connectivity.” Options include “always keeping the 2G radio off or ensuring employees are protected when traveling to specific high-risk locations” to counter 2G traffic interception and Person-in-the-Middle attacks.
Meanwhile, Android 14 introduces a setting to disable support for null-ciphered connections at the modem level. It’s available for devices that adopt the latest radio HAL (hardware abstraction layer), with Google expecting wide support for this measure “over the next few years as it is adopted by Android OEMs.”
Although all IP-based user traffic is protected and E2EE by the Android platform, cellular networks expose circuit-switched voice and SMS traffic. These two particular traffic types are strictly protected only by the cellular link layer cipher, which is fully controlled by the network without transparency to the user. In other words, the network decides whether traffic is encrypted and the user has no visibility into whether it is being encrypted.
The use of null ciphers in commercial networks can put voice and SMS traffic (with Google specifically highlighting One-Time Passwords/2FA) at risk for “trivial over the air interception.” Additionally, “some commercial Stingrays provide functionality to trick devices into believing ciphering is not supported by the network, thus downgrading the connection to a null cipher and enabling traffic interception.”
FTC: We use income earning auto affiliate links. More.


Comments