Google has issued a patch to handset manufacturers to block a security hole that could, in theory, allow almost any Android application to be turned into malware, reports ZDNet.
It doesn’t get much scarier than this. Bluebox Security claimed to have discovered a vulnerability in Android’s security model that could allow attackers to convert 99 percent of all applications into Trojan malware. Google has told ZDNet that the hole has been patched and that it has been released to original equipment manufacturers (OEM)s.
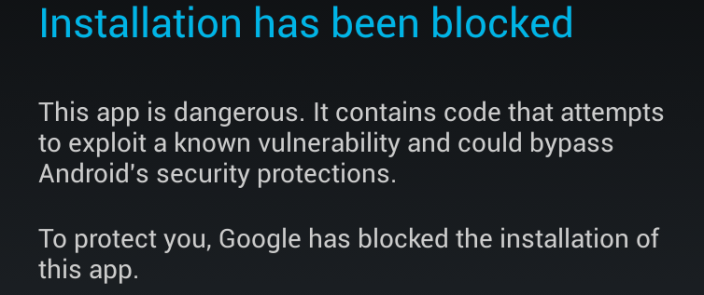
Handset and tablet owners will have to rely on the manufacturer to push the patch to their device, but the vulnerability isn’t as scary as it sounds. While it would in principle allow an attacker to change almost any application to malware without Android detecting the change, Google reports that there is no evidence of the exploit having actually been used.
“We have not seen any evidence of exploitation in Google Play or other app stores via our security scanning tools. Google Play scans for this issue – and Verify Apps provides protection for Android users who download apps to their devices outside of Play,” said Gina Scigliano, Google’s Android Communications Manager.
Via Techmeme